I did something stealthy-similar the other day using ngrok.io (a friend wanted to publish direct, but he didn’t have his router password so port-forwarding wasn’t an option)… From memory, here’s the process. Basically, ngrok runs on your PC and creates an outbound tunnel for an internal service.
Register an account at ngrok.io - free plan is fine
Receive an auth-token here and the command to store it: ngrok - secure introspectable tunnels to localhost
At the command line, run “ngrok tcp 2101” to stand a tunnel up forwarding port 2101 on the machine ublox is running (I’m assuming ublox and ngrok on same machine, use “ngrok tcp ubloxip:2101” if not).
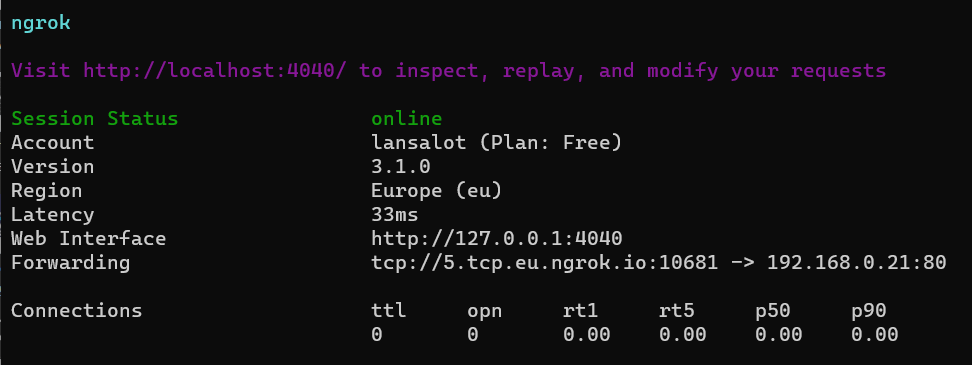
It’ll give you info on what the tunnel will be called, and this will change EVERY time you start ngrok unless you upgrade to a paid plan. Don’t have it handy, but it might be something like 5.tcp.eu.ngrok.io:14997, so that’s IP 5.tcp.eu.ngrok.io and port 14997 in AGO.
C:\Downloads> ngrok tcp 192.168.0.21:80
Worked a treat! here, 192.168.0.21 is my raspberry pi, and I’m running this from my PC.
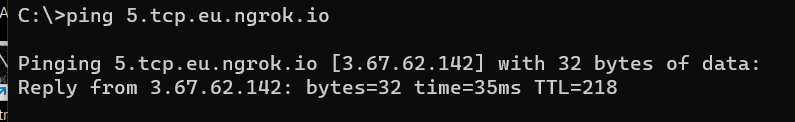
if your device won’t take host names, ping the ngrok DNS name to get the IP
here, 3.67.62.142
Also, I’ve written an rtkbase setup tutorial here: RTKBase - a tutorial